What Smart Investors Should Know About Crypto Mining
It takes pride in handling 100,000 s of mining gears and ASIC miners with a solitary system. It has an automobile coin switching feature that stays with one of the most successful formula to mine for the very best feasible profit. They additionally have a Cudo, OS for committed mining rigs. The setup resembles the mining OSes we’ve seen in this post.
 What is Malicious Cryptocurrency Mining? History and Prevention
What is Malicious Cryptocurrency Mining? History and PreventionSumming Up With cryptocurrency becoming a house term, crypto mining goes to an all-time high. There are plenty of crypto mining systems to aid a technical newbie as well as specialist miner alike. While it appears sensible to place the still computing power at mining, some degree of technological efficiency is necessary to churn revenues and prevent losses.
Regardless of its popularity, crypto mining isn’t for everyoneespecially the one with inadequate hardware ought to stay clear of mining. While cloud crypto mining seems the simplest approach to mine, Naturostockphotos.com the payments are not guaranteed.
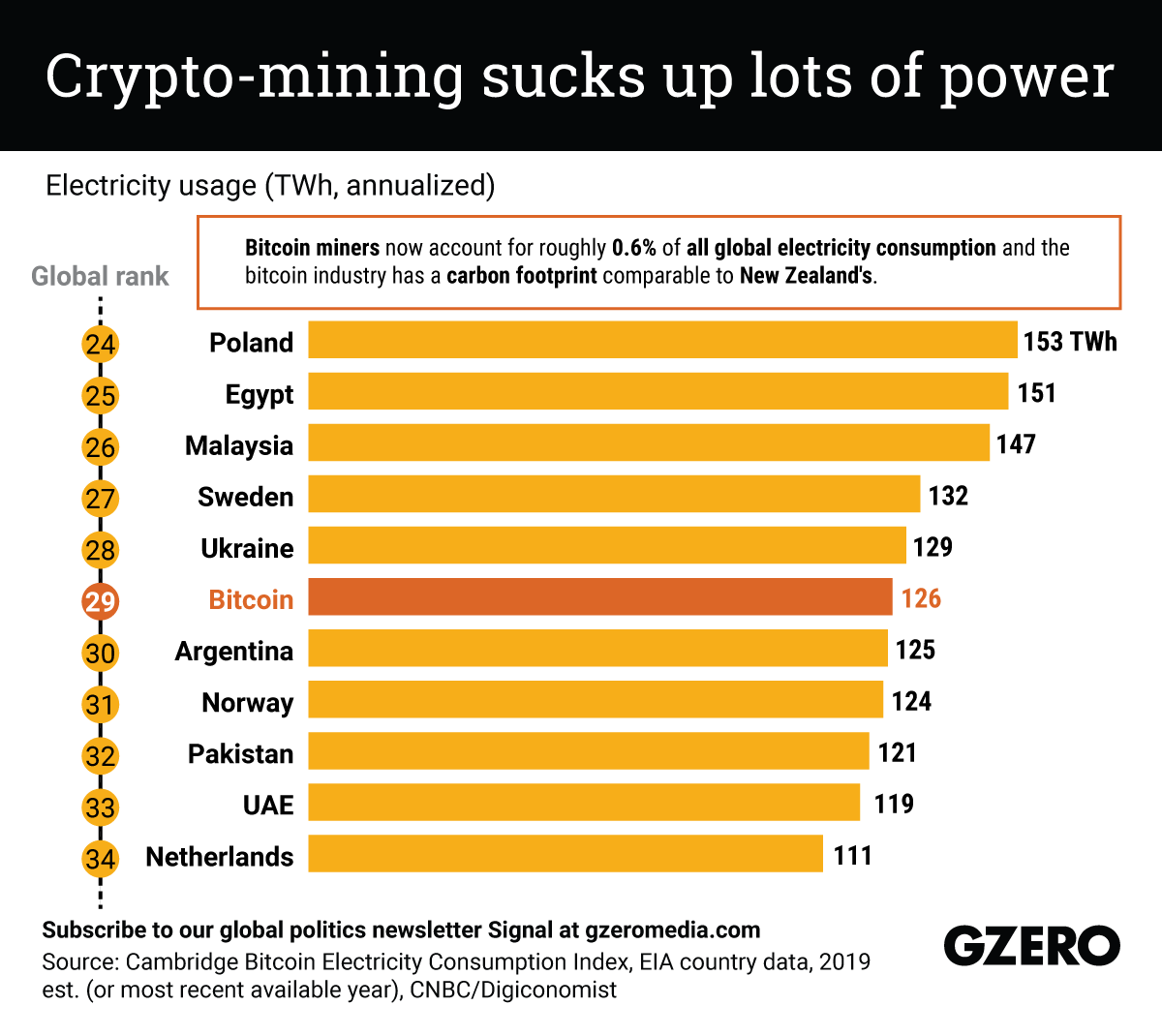
Bitcoin is simply among lots of cryptocurrencies, along with Monero and also Dogecoin, so the complete energy eaten by all cryptocurrencies is far greater. Offered that high-powered mining computer systems call for a lot handling power, crypto-mining is financially rewarding in nations with relatively economical electrical power. Nevertheless, the energy needed can cause serious consequences even closing down whole cities.
How to mine cryptos like bitcoin, ether, and doge
Mining rigs also generate a lot of warm and could have quickly caused a fire in the storehouse. This situation demonstrates the covert techniques opportunistic individuals may require to hijack corporate facilities with crypto-mining malware, along with the demand for a safety and security device which covers the entire digital estate as well as spots any type of new or unusual occasions.
Bitcoin mining is designed to be similar to gold mining in numerous ways. This «digital mining» is a computer system process that creates brand-new Bitcoin, along with tracking Bitcoin purchases and also possession. Bitcoin mining and gold mining are both energy intensive, and both have the possible to produce a good-looking monetary reward.
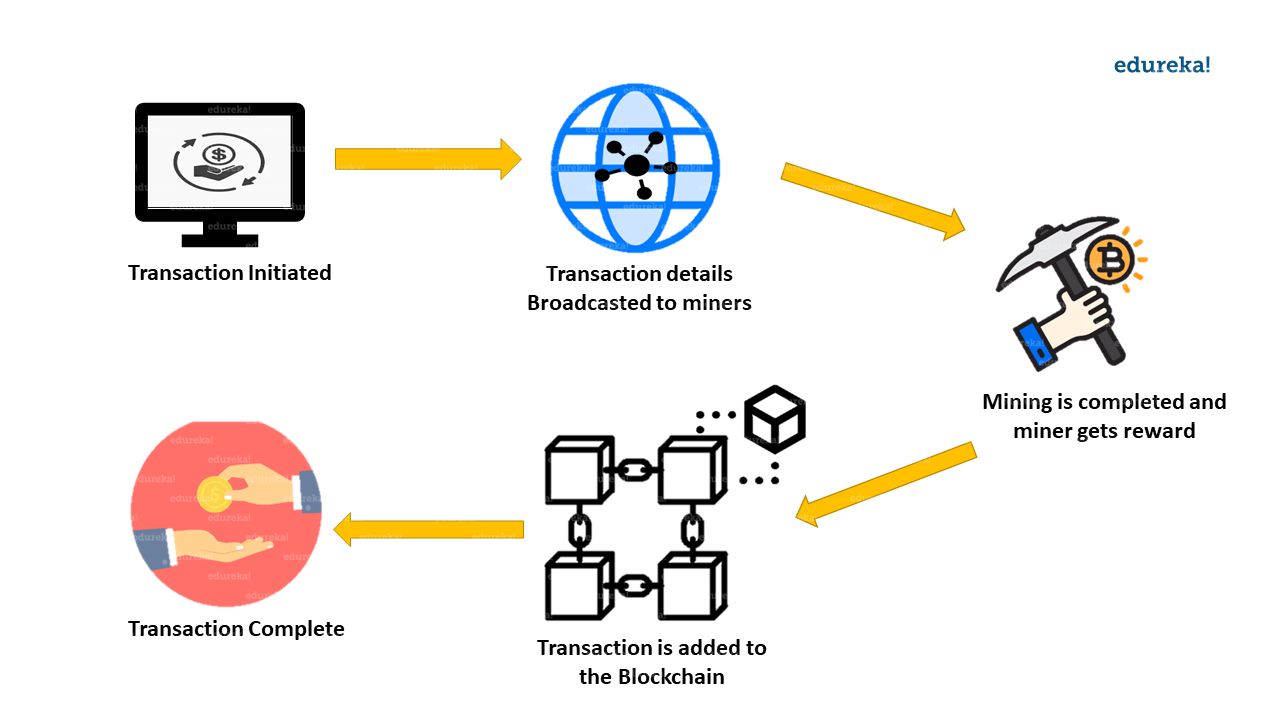
This mining procedure is called proof of work, because the very first miner to show that they have done the «job» of addressing a complex equation earns the right to process the latest block of Bitcoin transactions. After a miner successfully verifies a new block of deals, the block is distributed to all various other miners and also any kind of various other tool with a complete copy of the Bitcoin blockchain.
 What You Need for Mining Cryptocurrency — dummies
What You Need for Mining Cryptocurrency — dummiesRead More about
Bitcoin mining: Digital money printing with real world footprints?
http://socialvip.it/2022/01/25/learn-about-bitcoin-and-bitcoin-mining/
Hardware Damages Bitcoin mining is an extremely extreme process for hardware systems. If your mining system is established correctly, you shouldn’t need to bother with equipment damage past typical wear and also tear. Selecting the wrong equipment or running a mining arrangement with poor air flow can overheat as well as harm your machine.
How Does Bitcoin Mining Work?
Every year, the variety of Bitcoins created per block is halved. As soon as 21 million bitcoin have actually been minted, no brand-new bitcoins will be created. From that factor forward, Bitcoin miners will certainly benefit exclusively from deal costs. The reward for http://socialvip.It/2022/01/25/Learn-about-bitcoin-and-bitcoin-mining/ mining Bitcoin reduces as the quantity of unmined Bitcoin decreases. «Halving,» or a 50% reduction in benefits for Bitcoin miners, occurs each time an additional 210,000 blocks of Bitcoin are extracted.
It’s vital to track cryptocurrency deals for tax objectives, because ignoring tax obligation liabilities could obtain you in difficulty with Uncle Sam. Geographical Limitations Bitcoin and Bitcoin mining are not lawful everywhere.
 Blockchain Mining- All you need to know Edureka
Blockchain Mining- All you need to know EdurekaWhat is a good hashrate for Bitcoin mining? A mining computer system’s total hashrate, or computations per 2nd, signifies the mathematical processing power of a computer system or group of computers extracting Bitcoin. Higher hashrates prices are much better. As mining difficulty boosts, your mining rig requires a higher hashrate to complete with other miners.
Various other countries are joining the bandwagon, https://www.vetrina-eventi.com/ albeit partly: organizations and several of the public organizations in Switzerland, Norway, and the Netherlands. In a recent study, unique, active users of cryptocurrency budgets are fixed between 2. 9 and also 5. 8 million, a lot of which remain in The United States And Canada and also Europe. Yet what does the approval and also fostering of digital money involve on-line dangers? A whole lot, Www.Thewesternsolutions.com really.
What Smart Investors Should Know About Crypto Mining
While bitcoin mining isn’t naturally illegal (at least in several nations), it can entail a compromise if it doesn’t have the owner’s knowledge and consent. We discovered that devices running Windows had one of the most bitcoin mining activities, but also of note are: Systems on Macintosh OSes, topfund.icu including i, OS (i, https://thewhiteknight.org/ Phone 4 to i, http://socialvip.it/2022/01/25/Learn-about-bitcoin-and-bitcoin-mining/ Phone 7) Tools operate on Ubuntu OS, a by-product of Debian Linux OS Home routers Environment-monitoring gadgets, utilized in data facilities Android-run smart TVs and also mobile phones IP cams Print servers Gaming gaming consoles Cryptocurrency-mining malware can make sufferers a part of the trouble Cryptocurrency-mining malware can impair system efficiency and danger end individuals as well as organizations to info theft, www.stormbodykits.com hijacking, https://semanacompliance-campus.com/19251-2/ and also a huge selection of other malware.
Undoubtedly, their negative impact to the gadgets they infectand inevitably an organization’ asset or a customer’s datamakes them a reputable danger. There is no silver bullet for these malware, yet they can be reduced by complying with these ideal practices: Regularly updating your device with the current patches assists prevent assaulters from utilizing vulnerabilities as entrances right into the systems Changing or strengthening the gadget’s default credentials makes the gadget much less prone to unapproved access Allowing the gadget’s firewall program (for home routers), if available, or Http://Socialvip.It/2022/01/25/Learn-About-Bitcoin-And-Bitcoin-Mining/ deploying invasion discovery as well as avoidance systems to mitigate attack efforts Taking caution versus known strike vectors: socially crafted links, attachments or data from suspicious websites, uncertain third-party software/applications, as well as unwanted e-mails IT/system managers and info safety experts can likewise think about application whitelisting or similar security devices that stop dubious executables from running or mounting.













:max_bytes(150000):strip_icc()/dotdash_Final_How_Does_Bitcoin_Mining_Work_Dec_2020-02-5e922571968a41a29c1b01f5a15c2496.jpg)





