How Cloud Mining Is Making It Easier To Mine Cryptocurrency
It shows off managing 100,000 s of mining rigs as well as ASIC miners with a solitary system. It has an auto coin changing function that stays with one of the most successful formula to mine for the finest feasible profit. They additionally have a Cudo, OS for devoted mining gears. The setup is comparable to the mining OSes we have actually seen in this article.
 Virtual’ Data Center Power Startup VPS Eyes Crypto Mining Market Data Center Knowledge
Virtual’ Data Center Power Startup VPS Eyes Crypto Mining Market Data Center KnowledgeSumming Up With cryptocurrency ending up being a household term, crypto mining goes to an all-time high. There are many crypto mining platforms to help a technological beginner as well as professional miner alike. While it appears rational to place the idle computer power at mining, some degree of technological proficiency is necessary to spin earnings and prevent losses.
In spite of its appeal, crypto mining isn’t for everyoneespecially the one with inadequate hardware should prevent mining. While cloud crypto mining appears the most convenient technique to mine, the payouts are not ensured.
Bitcoin is simply one of several cryptocurrencies, alongside Monero and also Dogecoin, so the overall energy taken in by all cryptocurrencies is much greater. Considered that high-powered mining computers call for a lot processing power, crypto-mining is rewarding in nations with reasonably inexpensive electrical power. The energy needed can lead to severe repercussions also closing down entire cities.
Why the Biggest Bitcoin Mines Are in China
Mining gears likewise generate a great deal of warm and also could have easily caused a fire in the stockroom. This instance demonstrates the covert approaches opportunistic individuals may take to pirate corporate framework with crypto-mining malware, along with the requirement for a security device which covers the whole digital estate and also spots any kind of new or unusual events.
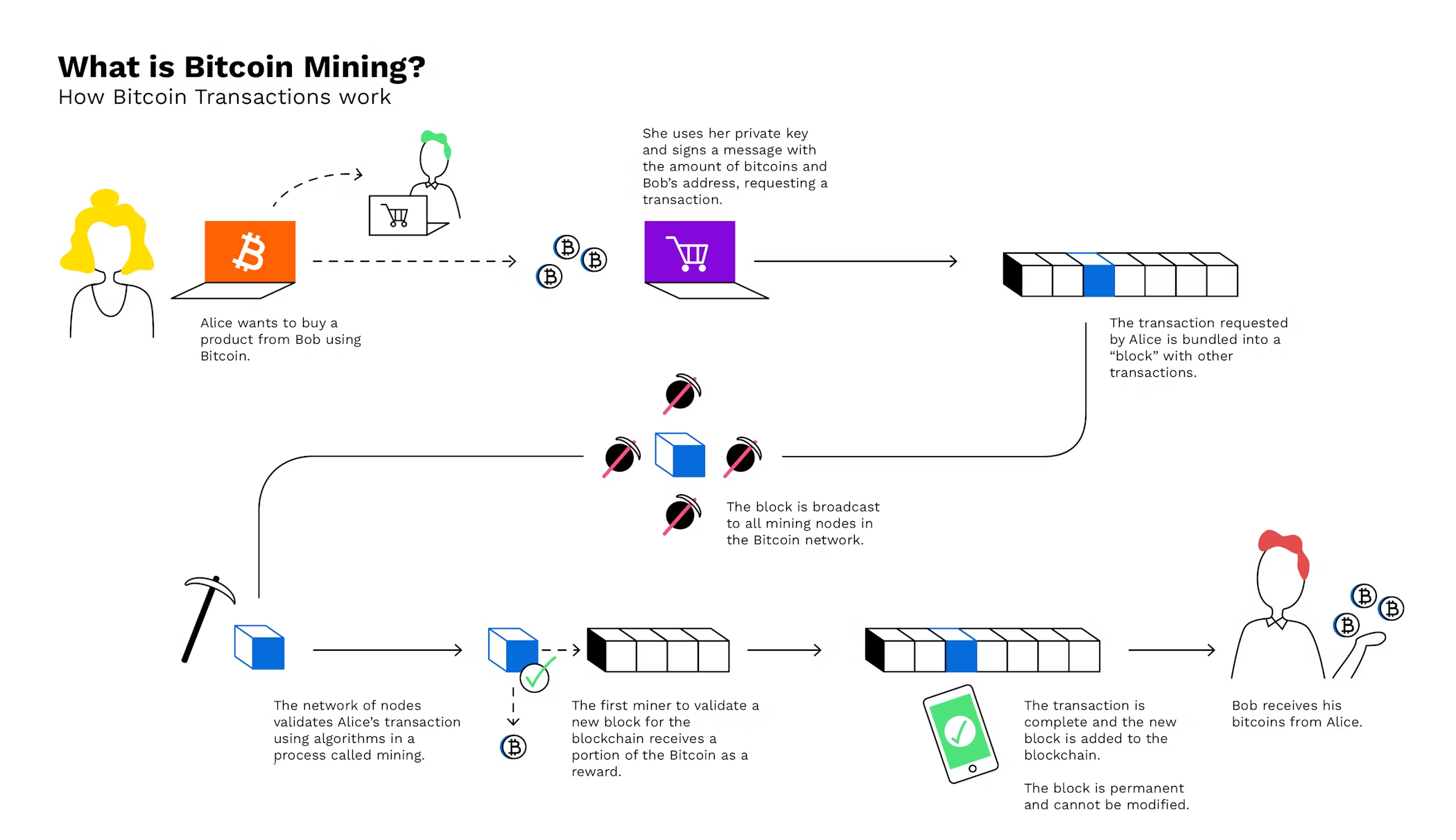
Bitcoin mining is made to be comparable to gold mining in lots of methods. This «digital mining» is a computer procedure that creates new Bitcoin, http://southernfilminstitute.org/community/profile/bessieoppen4265 in enhancement to tracking Bitcoin transactions as well as ownership. Bitcoin mining and gold mining are both energy extensive, as well as both have the potential to produce a good-looking financial reward.
This mining method is called proof of job, because the very first miner to confirm that they have actually done the «work» of solving a complex formula gains the right to refine the latest block of Bitcoin purchases. After a miner successfully verifies a new block of transactions, the block is dispersed to all other miners and also any type of various other tool with a full copy of the Bitcoin blockchain.
 Is crypto mining really moving to North America? · TechNode
Is crypto mining really moving to North America? · TechNodeRead also
Mining Facts — The Mining Association
http://Southernfilminstitute.org/community/profile/bessieoppen4265
Hardware Damage Bitcoin mining is an extremely extreme procedure for hardware units. If your mining system is established correctly, you shouldn’t need to bother with hardware damage past regular deterioration. Yet picking the incorrect equipment or running a mining arrangement with inadequate ventilation can overheat as well as damage your machine.
What Smart Investors Should Know About Crypto Mining
The reward for mining Bitcoin reduces as the quantity of unmined Bitcoin decreases. «Halving,» or a 50% decrease in benefits for Bitcoin miners, happens every time an additional 210,000 blocks of Bitcoin are mined.
It’s essential to track cryptocurrency transactions for tax objectives, because neglecting tax liabilities might obtain you in problem with Uncle Sam. Geographical Limitations Bitcoin and also Bitcoin mining are not lawful all over.
 The Basics of Cryptocurrency Mining, Explained in Plain English The Motley Fool
The Basics of Cryptocurrency Mining, Explained in Plain English The Motley FoolWhat is a great hashrate for Bitcoin mining? A mining computer system’s complete hashrate, or estimations per second, profhim.kz denotes the mathematical handling power of a computer or team of computer systems extracting Bitcoin. Higher hashrates prices are much better. As mining difficulty boosts, your mining rig requires a higher hashrate to contend with other miners.
, special, active individuals of cryptocurrency purses are fixed between 2. 9 and also 5. What does the approval and also adoption of electronic currencies have to do with on-line hazards?
Latest Bitcoin Mining News
While bitcoin mining isn’t naturally unlawful (at the very least in many countries), it can entail a compromise if it doesn’t have the owner’s expertise as well as consent. We discovered that devices running Windows had the most bitcoin mining activities, but likewise of note are: Solution on Macintosh OSes, including i, csiprojects.org OS (i, Phone 4 to i, Phone 7) Tools run on Ubuntu OS, a by-product of Debian Linux OS House routers Environment-monitoring tools, made use of in data facilities Android-run clever TVs and also mobile phones IP video cameras Print web servers Gaming consoles Cryptocurrency-mining malware can make sufferers a part of the problem Cryptocurrency-mining malware can hinder system performance and Medotrade.ru also danger end customers and also services to details theft, hijacking, https://gimgame.ru/ and a huge selection of other malware.
Their damaging effect to the gadgets they infectand eventually an organization’ possession or a customer’s datamakes them a legitimate risk. There is no silver bullet for these malware, http://Southernfilminstitute.org/community/profile/bessieoppen4265 however they can be alleviated by complying with these finest methods: On a regular basis upgrading your gadget with the most up to date patches aids prevent assailants from making use of vulnerabilities as doorways into the systems Changing or Http://Southernfilminstitute.Org/Community/Profile/Bessieoppen4265 strengthening the gadget’s default qualifications makes the device much less susceptible to unapproved access Making it possible for the device’s firewall program (for home routers), if offered, profhim.kz or releasing invasion discovery as well as avoidance systems to reduce incursion attempts Taking caution versus known strike vectors: socially engineered web links, accessories or https://forum.oumnaturel.com data from suspicious web sites, uncertain third-party software/applications, and unrequested e-mails IT/system managers as well as details protection specialists can also take into consideration application whitelisting or similar security systems that prevent dubious executables from running or Http://Southernfilminstitute.Org/Community/Profile/Bessieoppen4265 setting up.